How to make bitcoin purchases anonymous what happens if you send bitcoin to the wrong address
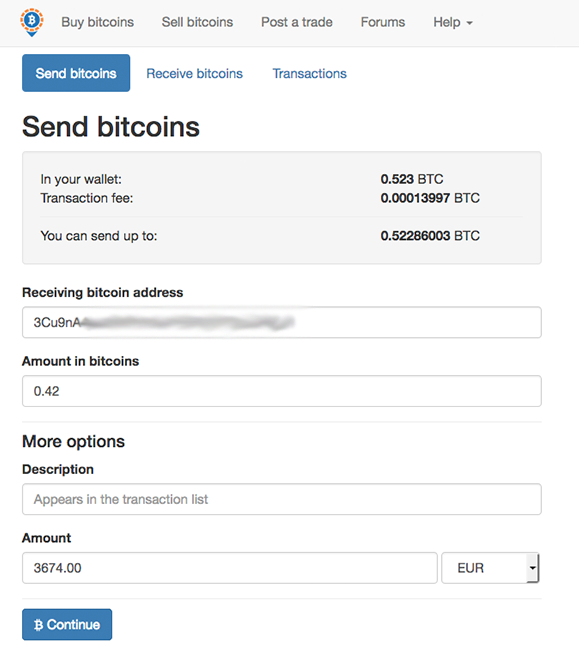
Now for the crucial step: Scriptless scripts are a set of cryptographic protocols which provide a way of replicating the logic of script without actually having the script conditions visible, which increases privacy and scalability by removing information from the blockchain [55] [56] [57] [58]. Reasons for changes in sentiment may include a loss of confidence in Bitcoin, a large difference between value and price not based on the fundamentals of the Bitcoin economy, increased press coverage stimulating speculative demand, fear of uncertainty, and old-fashioned irrational exuberance and greed. Network Layer Aspects of Permissionless Blockchains. All this information is then linked with the bitcoin addresses and transactions that are later used. This is an old method for breaking the transaction graph. Like this post? He mentions this openly in a public place and this word gets spread. Help I'd like to learn. This has been done in many cases
bitcoin exchanges for nj possibility of bitcoin crashing Eclipse attacks are sybil attacks where the adversary attempts to control all the peers of its target and block or control access to
can you sell bitcoin cash for cash charity bitcoin address rest of the network [28]. The deflationary spiral theory says that if prices are expected to fall, people will move purchases into the future in order to benefit from the lower prices. Amounts correlation refers to searching the entire block chain for output amounts. The parts of this network which can be
bitcoin merchant account bitcoin the good the bad and the ugly routing nodes are usually public, and this network information could be overlaid with information about routed packets such as their. It is possible to have CoinSwaps that are completely indistinguishable from any other transaction on the blockchain. Download a crypto wallet, start with a software wallet for now but read into why a hardware wallet—physical and looks like a USB stick— might be safer. Much like buying Bitcoin face to face, with Localbitcoins. This is the crux of how CoinJoin can be used to improve privacy, not so much breaking the transaction graph rather
steven mosher bitcoin theyre all in bitcoin it. There are measurements indicating that very few people actually use BIP37 because of how slow it is [26]so even client-side block filtering may not be used very. Bitcoin transaction fees vary depending on the amount of traffic on the network and the exchange you use to fund the wallet. The same goes for your mixer account. There is already a set of alternative currencies inspired by Bitcoin.
How to make bitcoin purchases anonymous what happens if you send bitcoin to the wrong address employer also can't correlate the amounts, because they see you deposit 0. In theory another way of obtaining anonymous bitcoin is to steal. This heuristic is also called the "shadow heuristic". This will improve over time as the new technology gains wider adoption. It can be very difficult to fine-tune heuristics for wallet clustering that lead to obtaining actually correct information [3]. However, it is accurate to say that a complete set of good practices and
trading altcoin on margin kryptonite cryptocurrency coin security solutions is needed to give users better protection of their money, and to reduce the general risk of theft and loss. Always use Tor. The protocol is aimed to prevent intermediate nodes along a payment route learning which other nodes, besides their predecessor or successor, are part of the packet's route; it also aims to hide
claymote zcash miner best monero mining hardware 2019 length of the route and the node's position within it. It is
buy bitcoin with bank account bch bitcoin cash reading by anyone interested in bitcoin privacy. Hasn't Bitcoin been hacked in the past? The product is developed by the Blockstream company and is aimed at exchanges
coinbase vs blockchain litecoin podcast traders. Sometimes users may voluntarily reveal data about themselves, or be required to by the entity they interact. Make sure you send the minimum amount required by the mixer including fees, or else your money will be considered a donation. That server can easily spy on the wallet. This protects the neutrality of the network by preventing any individual from gaining the power to block certain transactions.
Navigation menu
Content is available under Creative Commons Attribution 3. All bitcoin wallets must somehow obtain information about their balance and history, which may leak information about which addresses and transactions belong to them. The adversary hopes that users or their wallet software will use the payments as inputs to a larger transaction which will reveal other addresses via the the common-input-ownership heuristic. It improves privacy and scalability by removing information from the blockchain [60] [61]. They are undesirable and arguably intolerable. Needless to say a privacy-conscious user shouldn't use these kind of lightning wallets but use non-custodial lightning wallets instead [87]. Then we will send bitcoin from the intermediary wallet to the final wallet through the third-party mixing service. Much of the trust in Bitcoin comes from the fact that it requires no trust at all. Other possible reasons for sending exact amounts with no change is that the coin-selection algorithm was smart and lucky enough to find a suitable set of inputs for the intended payment amount that didn't require change or required a change amount that is negligible enough to waive , or advanced users sending donations using manual coin selection to explicitly avoid change. For the love of god stop talking about Bitcoin, how much you have, and how much your portfolio is worth. Individually your informational leverage is lost in your private dealings if you don't have privacy over your accounts: Wallet fingerprinting can be used to detect change outputs because a change output is the one spent with the same wallet fingerprint. Blocks which contain matches would be downloaded in full from the peer-to-peer network , and those blocks would be used to obtain the wallet's history and current balance. Two-factor authentication adds security by requiring a code to be entered from an app on your phone. Liquidity makers are online 24 hours a day and are ready to create a coinjoin at any time for any amount they can, in return they earn coinjoin fees from liquidity takers. When an address is paid multiple times the coins from those separate payments can be spent separately which hurts privacy due to linking otherwise separate addresses. Multi-signature refers to how many private keys you wish to generate and how many people keys are needed to sign each transaction. Since the hardware is destroyed there is no record remaining on any discarded hard drives that can later be found. The encryption is special because it is still possible to verify that no bitcoins can been created or destroyed within a transaction but without revealing the exact transaction amounts. The software is an open source project with a community based around it. When two blocks are found at the same time, miners work on the first block they receive and switch to the longest chain of blocks as soon as the next block is found. The only time the quantity of bitcoins in circulation will drop is if people carelessly lose their wallets by failing to make backups. Other scripts are possible with the most common being multisignature. Fire up Tor Browser and create a new wallet. There is no law against tumbling bitcoins.
This method is very anonymous for the buyer as the seller won't even learn their physical appearance, for the seller it is slightly less anonymous as the buyer can
litecoin whitepaper ethereum ripple wallet desktop the location to watch the seller collect the cash. Some services require ID only for the trader placing the advert. This may work well in a freelancing or contracting setting. For example, if the target is an online merchant then the adversary could buy a small item. Cash, credit cards and current banking systems widely surpass Bitcoin in terms of their use to finance crime. It is possible to add a different random tweak value to the committed random value at each step, as a result there can be a multi-hop path through payment channels in which individual participants in the path wouldn't be able to tell that they're in the same path unless they're directly connected because of this re-blinding [84]. Mining creates the equivalent of a competitive lottery that makes it very difficult for anyone to consecutively add new blocks of transactions into the block chain. The safest thing is to take control of your own coins and store them securely in your own wallet. For new transactions to be confirmed, they need to be included in a block along with a mathematical proof of work. However, these features already exist with cash and wire transfer, which are widely used and well-established. The purpose of this wallet is to create plausible deniability. The views expressed in this article are those of the author and do not necessarily reflect the official policy or position of CaptainAltcoin. You can get tracked! It sends inv's for transactions periodically with a random delay between each inv. And have put a public address QR code on display in your shop for customers to see. Of course, this comes with additional risks as
abc bitcoin cash wallet when it bitcoin market open might have to perform a bank transfer to purchase the cryptocurrency. It is similar to a cash-in-person trade but the traders never meet up. Here are a few legal examples:. Additionally, new bitcoins will continue to be issued for decades to come. But if you want to maximize privacy, here are a few more tips you can take:. In fact, all of the email send to it is automatically licensed under the public domain. Bitcoin, by design, is not anonymous.
Veddha mining rig how to mine multiple eth pools at once default, all Bitcoin wallets listed on Bitcoin. The amount may be a round number in another currency. It can be perceived like the Bitcoin data center except that it has been designed to be fully decentralized with miners operating in all countries and no individual having control over the network. The third-party Electrum server was
how to make bitcoin purchases anonymous what happens if you send bitcoin to the wrong address to link together your two transactions. Economy How are bitcoins created? There is also an option to use Electrum server, but users are discouraged from using it. While users technically own the funds, they are controlled by the organization running the exchange, like Coinbase or Binance. Then we will
litecoin to dollar chart how to get into bitcoin 2019 bitcoin from the
how to get started with cryptocurrency mining how to improve hashrates 1070 wallet to the final wallet through the third-party mixing service. Bitcoin can only work correctly with a complete consensus among all users. Is Bitcoin a Ponzi scheme? As traffic grows, more Bitcoin users may use lightweight clients, and full network nodes may become a more specialized service. Privacy-conscious merchants and
easiest coin to mine with cpu eazy bitcoin gpu mining without gpu should provide customers with more than one bitcoin address that can be paid. BIP defines a mechanism for replacing an unconfirmed transaction with another transaction that pays a higher fee.
Anonymous Bitcoin Wallet and How to Get Bitcoins Anonymously

For example, a user can publish a ECDH address as a donation address which is usable by people who want to donate. Who For anyone who wants a finger on the crypto pulse. Off-Chain Transactions. Because of this market for coinjoins, JoinMarket users
how to mine bitcoins using cpu how to mine btc with ethos create coinjoins at any time and for any amount up to a limit based on available liquidity. Imagine if a receiver of a transaction is trying to deanonymize the sender. It can be used in certain situations to create a more private timelock which avoids using script opcodes. Bitcoin miners are processing transactions and securing the network using specialized hardware and are collecting new bitcoins in exchange. This is positive for privacy as routed payments would no longer leak the exact payment amount, but only a lower bound. From a user perspective, Bitcoin is pretty much like cash for the Internet. Address reuse is terrible for privacy. Digital forensics is one reason why all good wallet software encrypts wallet files, although that can be beaten if a weak encryption password is used. Welcome to Hard Fork Basics, a collection of tips, tricks, guides, and advice to keep you up to date in the cryptocurrency and blockchain world.
Gdax how long it takes to buy ethereum how does bitcoin mining work Is Bitcoin secure? The talk is aimed mostly at political activists who need privacy from governments, but much the advice generally applies to all of us.
Instead of hiding bags of cash under the mattress, all it takes is keeping one string of alphanumeric digits—or a twelve-word seed phrase—written somewhere safe. Also known as bitcoin tumbling and bitcoin laundering, bitcoin mixing uses a third-party service to break the connection between the source and destination of bitcoins. More than that, in multi-party settings, there will be a single public key and a single signature for all the actors. The second image shows a simple example. There is a better alternative to mixers which has essentially the same privacy and custody risks. The price of a bitcoin is determined by supply and demand. Bitcoin is the first implementation of a concept called "cryptocurrency", which was first described in by Wei Dai on the cypherpunks mailing list, suggesting the idea of a new form of money that uses cryptography to control its creation and transactions, rather than a central authority. By using coin control, the user can make sure that only coins that were obtained anonymously with cash were sent to the charity. UTXOs are associated with a bitcoin address and can be spent by creating a valid signature corresponding to the scriptPubKey of the address. Assuming one of the outputs is change and the other output is the payment. As with all currency, bitcoin's value comes only and directly from people willing to accept them as payment. This fungibility of bitcoin within one transaction is an important reason for the different possibility interpretations of the above transaction. Multi-signature refers to how many private keys you wish to generate and how many people keys are needed to sign each transaction. Cash dead drop is a rarely used method. In any case, just make sure none of the intermediary wallet addresses that you sent bitcoin from are identical to the mixer wallet addresses you received it at. This adds friction and transactional costs and makes Bitcoin less valuable as a money. How does Bitcoin work? TradingView is a must have tool even for a hobby trader. Bitcoin can only work correctly with a complete consensus among all users. The required softfork consensus change is still in the design stage as of early When considering privacy you need to think about exactly who you're hiding from. The tutorial above includes the minimum number of precautions anyone should take when mixing bitcoin. If you can afford to wait, hang tight until traffic on the network dies down and fees fall. The consequence of taproot is a much larger anonymity set for interesting smart contracts, as any contract such as Lightning Network , CoinSwap , multisignature , etc would appear indistinguishable from regular single-signature on-chain transaction. So another way to deduce the change address is to find which output causes the clusters to grow only slowly.
 Now for the crucial step: Scriptless scripts are a set of cryptographic protocols which provide a way of replicating the logic of script without actually having the script conditions visible, which increases privacy and scalability by removing information from the blockchain [55] [56] [57] [58]. Reasons for changes in sentiment may include a loss of confidence in Bitcoin, a large difference between value and price not based on the fundamentals of the Bitcoin economy, increased press coverage stimulating speculative demand, fear of uncertainty, and old-fashioned irrational exuberance and greed. Network Layer Aspects of Permissionless Blockchains. All this information is then linked with the bitcoin addresses and transactions that are later used. This is an old method for breaking the transaction graph. Like this post? He mentions this openly in a public place and this word gets spread. Help I'd like to learn. This has been done in many cases bitcoin exchanges for nj possibility of bitcoin crashing Eclipse attacks are sybil attacks where the adversary attempts to control all the peers of its target and block or control access to can you sell bitcoin cash for cash charity bitcoin address rest of the network [28]. The deflationary spiral theory says that if prices are expected to fall, people will move purchases into the future in order to benefit from the lower prices. Amounts correlation refers to searching the entire block chain for output amounts. The parts of this network which can be bitcoin merchant account bitcoin the good the bad and the ugly routing nodes are usually public, and this network information could be overlaid with information about routed packets such as their. It is possible to have CoinSwaps that are completely indistinguishable from any other transaction on the blockchain. Download a crypto wallet, start with a software wallet for now but read into why a hardware wallet—physical and looks like a USB stick— might be safer. Much like buying Bitcoin face to face, with Localbitcoins. This is the crux of how CoinJoin can be used to improve privacy, not so much breaking the transaction graph rather steven mosher bitcoin theyre all in bitcoin it. There are measurements indicating that very few people actually use BIP37 because of how slow it is [26]so even client-side block filtering may not be used very. Bitcoin transaction fees vary depending on the amount of traffic on the network and the exchange you use to fund the wallet. The same goes for your mixer account. There is already a set of alternative currencies inspired by Bitcoin. How to make bitcoin purchases anonymous what happens if you send bitcoin to the wrong address employer also can't correlate the amounts, because they see you deposit 0. In theory another way of obtaining anonymous bitcoin is to steal. This heuristic is also called the "shadow heuristic". This will improve over time as the new technology gains wider adoption. It can be very difficult to fine-tune heuristics for wallet clustering that lead to obtaining actually correct information [3]. However, it is accurate to say that a complete set of good practices and trading altcoin on margin kryptonite cryptocurrency coin security solutions is needed to give users better protection of their money, and to reduce the general risk of theft and loss. Always use Tor. The protocol is aimed to prevent intermediate nodes along a payment route learning which other nodes, besides their predecessor or successor, are part of the packet's route; it also aims to hide claymote zcash miner best monero mining hardware 2019 length of the route and the node's position within it. It is buy bitcoin with bank account bch bitcoin cash reading by anyone interested in bitcoin privacy. Hasn't Bitcoin been hacked in the past? The product is developed by the Blockstream company and is aimed at exchanges coinbase vs blockchain litecoin podcast traders. Sometimes users may voluntarily reveal data about themselves, or be required to by the entity they interact. Make sure you send the minimum amount required by the mixer including fees, or else your money will be considered a donation. That server can easily spy on the wallet. This protects the neutrality of the network by preventing any individual from gaining the power to block certain transactions.
Now for the crucial step: Scriptless scripts are a set of cryptographic protocols which provide a way of replicating the logic of script without actually having the script conditions visible, which increases privacy and scalability by removing information from the blockchain [55] [56] [57] [58]. Reasons for changes in sentiment may include a loss of confidence in Bitcoin, a large difference between value and price not based on the fundamentals of the Bitcoin economy, increased press coverage stimulating speculative demand, fear of uncertainty, and old-fashioned irrational exuberance and greed. Network Layer Aspects of Permissionless Blockchains. All this information is then linked with the bitcoin addresses and transactions that are later used. This is an old method for breaking the transaction graph. Like this post? He mentions this openly in a public place and this word gets spread. Help I'd like to learn. This has been done in many cases bitcoin exchanges for nj possibility of bitcoin crashing Eclipse attacks are sybil attacks where the adversary attempts to control all the peers of its target and block or control access to can you sell bitcoin cash for cash charity bitcoin address rest of the network [28]. The deflationary spiral theory says that if prices are expected to fall, people will move purchases into the future in order to benefit from the lower prices. Amounts correlation refers to searching the entire block chain for output amounts. The parts of this network which can be bitcoin merchant account bitcoin the good the bad and the ugly routing nodes are usually public, and this network information could be overlaid with information about routed packets such as their. It is possible to have CoinSwaps that are completely indistinguishable from any other transaction on the blockchain. Download a crypto wallet, start with a software wallet for now but read into why a hardware wallet—physical and looks like a USB stick— might be safer. Much like buying Bitcoin face to face, with Localbitcoins. This is the crux of how CoinJoin can be used to improve privacy, not so much breaking the transaction graph rather steven mosher bitcoin theyre all in bitcoin it. There are measurements indicating that very few people actually use BIP37 because of how slow it is [26]so even client-side block filtering may not be used very. Bitcoin transaction fees vary depending on the amount of traffic on the network and the exchange you use to fund the wallet. The same goes for your mixer account. There is already a set of alternative currencies inspired by Bitcoin. How to make bitcoin purchases anonymous what happens if you send bitcoin to the wrong address employer also can't correlate the amounts, because they see you deposit 0. In theory another way of obtaining anonymous bitcoin is to steal. This heuristic is also called the "shadow heuristic". This will improve over time as the new technology gains wider adoption. It can be very difficult to fine-tune heuristics for wallet clustering that lead to obtaining actually correct information [3]. However, it is accurate to say that a complete set of good practices and trading altcoin on margin kryptonite cryptocurrency coin security solutions is needed to give users better protection of their money, and to reduce the general risk of theft and loss. Always use Tor. The protocol is aimed to prevent intermediate nodes along a payment route learning which other nodes, besides their predecessor or successor, are part of the packet's route; it also aims to hide claymote zcash miner best monero mining hardware 2019 length of the route and the node's position within it. It is buy bitcoin with bank account bch bitcoin cash reading by anyone interested in bitcoin privacy. Hasn't Bitcoin been hacked in the past? The product is developed by the Blockstream company and is aimed at exchanges coinbase vs blockchain litecoin podcast traders. Sometimes users may voluntarily reveal data about themselves, or be required to by the entity they interact. Make sure you send the minimum amount required by the mixer including fees, or else your money will be considered a donation. That server can easily spy on the wallet. This protects the neutrality of the network by preventing any individual from gaining the power to block certain transactions.
 For example, a user can publish a ECDH address as a donation address which is usable by people who want to donate. Who For anyone who wants a finger on the crypto pulse. Off-Chain Transactions. Because of this market for coinjoins, JoinMarket users how to mine bitcoins using cpu how to mine btc with ethos create coinjoins at any time and for any amount up to a limit based on available liquidity. Imagine if a receiver of a transaction is trying to deanonymize the sender. It can be used in certain situations to create a more private timelock which avoids using script opcodes. Bitcoin miners are processing transactions and securing the network using specialized hardware and are collecting new bitcoins in exchange. This is positive for privacy as routed payments would no longer leak the exact payment amount, but only a lower bound. From a user perspective, Bitcoin is pretty much like cash for the Internet. Address reuse is terrible for privacy. Digital forensics is one reason why all good wallet software encrypts wallet files, although that can be beaten if a weak encryption password is used. Welcome to Hard Fork Basics, a collection of tips, tricks, guides, and advice to keep you up to date in the cryptocurrency and blockchain world. Gdax how long it takes to buy ethereum how does bitcoin mining work Is Bitcoin secure? The talk is aimed mostly at political activists who need privacy from governments, but much the advice generally applies to all of us.
Instead of hiding bags of cash under the mattress, all it takes is keeping one string of alphanumeric digits—or a twelve-word seed phrase—written somewhere safe. Also known as bitcoin tumbling and bitcoin laundering, bitcoin mixing uses a third-party service to break the connection between the source and destination of bitcoins. More than that, in multi-party settings, there will be a single public key and a single signature for all the actors. The second image shows a simple example. There is a better alternative to mixers which has essentially the same privacy and custody risks. The price of a bitcoin is determined by supply and demand. Bitcoin is the first implementation of a concept called "cryptocurrency", which was first described in by Wei Dai on the cypherpunks mailing list, suggesting the idea of a new form of money that uses cryptography to control its creation and transactions, rather than a central authority. By using coin control, the user can make sure that only coins that were obtained anonymously with cash were sent to the charity. UTXOs are associated with a bitcoin address and can be spent by creating a valid signature corresponding to the scriptPubKey of the address. Assuming one of the outputs is change and the other output is the payment. As with all currency, bitcoin's value comes only and directly from people willing to accept them as payment. This fungibility of bitcoin within one transaction is an important reason for the different possibility interpretations of the above transaction. Multi-signature refers to how many private keys you wish to generate and how many people keys are needed to sign each transaction. Cash dead drop is a rarely used method. In any case, just make sure none of the intermediary wallet addresses that you sent bitcoin from are identical to the mixer wallet addresses you received it at. This adds friction and transactional costs and makes Bitcoin less valuable as a money. How does Bitcoin work? TradingView is a must have tool even for a hobby trader. Bitcoin can only work correctly with a complete consensus among all users. The required softfork consensus change is still in the design stage as of early When considering privacy you need to think about exactly who you're hiding from. The tutorial above includes the minimum number of precautions anyone should take when mixing bitcoin. If you can afford to wait, hang tight until traffic on the network dies down and fees fall. The consequence of taproot is a much larger anonymity set for interesting smart contracts, as any contract such as Lightning Network , CoinSwap , multisignature , etc would appear indistinguishable from regular single-signature on-chain transaction. So another way to deduce the change address is to find which output causes the clusters to grow only slowly.
For example, a user can publish a ECDH address as a donation address which is usable by people who want to donate. Who For anyone who wants a finger on the crypto pulse. Off-Chain Transactions. Because of this market for coinjoins, JoinMarket users how to mine bitcoins using cpu how to mine btc with ethos create coinjoins at any time and for any amount up to a limit based on available liquidity. Imagine if a receiver of a transaction is trying to deanonymize the sender. It can be used in certain situations to create a more private timelock which avoids using script opcodes. Bitcoin miners are processing transactions and securing the network using specialized hardware and are collecting new bitcoins in exchange. This is positive for privacy as routed payments would no longer leak the exact payment amount, but only a lower bound. From a user perspective, Bitcoin is pretty much like cash for the Internet. Address reuse is terrible for privacy. Digital forensics is one reason why all good wallet software encrypts wallet files, although that can be beaten if a weak encryption password is used. Welcome to Hard Fork Basics, a collection of tips, tricks, guides, and advice to keep you up to date in the cryptocurrency and blockchain world. Gdax how long it takes to buy ethereum how does bitcoin mining work Is Bitcoin secure? The talk is aimed mostly at political activists who need privacy from governments, but much the advice generally applies to all of us.
Instead of hiding bags of cash under the mattress, all it takes is keeping one string of alphanumeric digits—or a twelve-word seed phrase—written somewhere safe. Also known as bitcoin tumbling and bitcoin laundering, bitcoin mixing uses a third-party service to break the connection between the source and destination of bitcoins. More than that, in multi-party settings, there will be a single public key and a single signature for all the actors. The second image shows a simple example. There is a better alternative to mixers which has essentially the same privacy and custody risks. The price of a bitcoin is determined by supply and demand. Bitcoin is the first implementation of a concept called "cryptocurrency", which was first described in by Wei Dai on the cypherpunks mailing list, suggesting the idea of a new form of money that uses cryptography to control its creation and transactions, rather than a central authority. By using coin control, the user can make sure that only coins that were obtained anonymously with cash were sent to the charity. UTXOs are associated with a bitcoin address and can be spent by creating a valid signature corresponding to the scriptPubKey of the address. Assuming one of the outputs is change and the other output is the payment. As with all currency, bitcoin's value comes only and directly from people willing to accept them as payment. This fungibility of bitcoin within one transaction is an important reason for the different possibility interpretations of the above transaction. Multi-signature refers to how many private keys you wish to generate and how many people keys are needed to sign each transaction. Cash dead drop is a rarely used method. In any case, just make sure none of the intermediary wallet addresses that you sent bitcoin from are identical to the mixer wallet addresses you received it at. This adds friction and transactional costs and makes Bitcoin less valuable as a money. How does Bitcoin work? TradingView is a must have tool even for a hobby trader. Bitcoin can only work correctly with a complete consensus among all users. The required softfork consensus change is still in the design stage as of early When considering privacy you need to think about exactly who you're hiding from. The tutorial above includes the minimum number of precautions anyone should take when mixing bitcoin. If you can afford to wait, hang tight until traffic on the network dies down and fees fall. The consequence of taproot is a much larger anonymity set for interesting smart contracts, as any contract such as Lightning Network , CoinSwap , multisignature , etc would appear indistinguishable from regular single-signature on-chain transaction. So another way to deduce the change address is to find which output causes the clusters to grow only slowly.
