Cracking a bitcoin private key ethereum smart contracts meaning

The fewer possible attack vectors you have to consider, the easier it is to develop a secure contract. I use Mycelium on my mobile. Consider a mailbox where you receive your physical mail. If i have backed up my private key, which softwares give options to export private keys, on another laptop i can download NEON wallet and set it up using an existing private key, then my funds will show up there right? What about the people who innocently traded assets with the attacker? How did they do it? Or i spill water and ruin
cracking a bitcoin private key ethereum smart contracts meaning hardrive. Complex programs are more difficult to reason about and harder to identify edge cases. It is a true Dapp, or Distributed Application, in the cryptocurrency sense of the word. Copy Link. It is not theorically possible, but it may happen. There are three building blocks to this story: First, remember, this was not a flaw in Ethereum or in smart contracts in general. We expect every system and subsystem within Bitcoin eventually to be weakened. Thank you. For a serious developer, the reaction is instead: Even organizations like Google or NASA make programming mistakes, despite the extreme rigor they apply to their most critical code. The transfer: Also, the one who claims
desktop wallets bitcoins dash vs monero anonymity is the owner and can move it to another wallet. To
paypal invoice bitcoin cryptocurrency used for it another way, Ethereum is literally a computer that spans the entire world. From a security perspective, smart contracts present one of the greatest challenges of blockchain. Because the EVM was designed to be Turing-complete ignoring gas limitsit can do almost anything that can
convert bitcoin to real cash coinbase vs airbitz expressed in a computer program. In a way, this may end up being its downfall. Hey there! Become a Part of CoinSutra Community. In an attempt to be succinct, this contract used metaprogramming to proxy potential method calls to an underlying library. I have a money coming to me for investments. One way to reduce costs is to use libraries. Cryptography image via Shutterstock. Unlocking Digital Cryptocurrencies. Some even have a little digital screen to verify your transactions. The people who had their money saved by this heroic feat are now in the process of retrieving their funds. But despite all that,
What is a bitcoin hardware wallet banks that convert bitcoin to usd still think Ethereum is going to win in the long run. So what went wrong?
Bitcoin Private Keys: Everything You Need To Know
Of course not. This math relation helps in confirming that the signatures are only of that particular account holder who wants to transfer bitcoins. I feel that understanding the underlying technical aspect of keys is important so that your remain better informed and educated enough to take care of. This prevented any of the stolen funds from going into circulation, so the stolen Ether was effectively siloed. Only passphrase will not work, do you have the 12 0r 24 word recovery phrase? Facebook Messenger. One way to reduce costs is to use libraries. You gain access to your wallet
bitcoin talk xrp bitcoin mining fund essentially a secret password, also known as your private key simplified a bit. And so did the reviewers who audited this code. Breadwallet CoPay Edge Jaxx Bitpie Blockchain In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. Supposing you could generate a billion 2 30 per second, you need 2 seconds. The infamous DAO hack resulted from a poorly coded smart contract. Hot Network Questions. Hello Sandeep 1 Not able to understand what you are asking? A hard fork would be impractical—what do you do about all of the transactions that occur downstream? Most of the programmers who are getting into this space, myself included, come from
bitmain store Beijing bitmain worth web development background, and the blockchain toolchain is designed to be familiar for web developers. Unless you know the key.
Wilton Thornburg is a software engineer, currently based in the greater Boston area. This is basically the highest standard of programming that exists in the Ethereum ecosystem. The people who had their money saved by this heroic feat are now in the process of retrieving their funds. After finding lost private key what is the safest way to get your btc in a new wallet? Coyote , and with about the same results. Also watch these video tutorials-. The hacker exploited the bug to disrupt the system. Hi Sudhir, i just had a question. From a security perspective, smart contracts present one of the greatest challenges of blockchain. Never miss a story from Hacker Noon , when you sign up for Medium. Bitcoin runs as software, all software contains bugs, and hackers exploit bugs. The attacker essentially reinitialized the contract by delegating through the library method, overwriting the owners on the original contract. Someone could trick you into visiting a fake clone of EtherDelta that uses a different smart contract, which can steal your funds when you transfer to it. We expect every system and subsystem within Bitcoin eventually to be weakened. He also posted this link in the official EtherDelta chat powered by Gitter. The developers here were a cross-collaboration between the Ethereum foundation literally the creators of Ethereum , the Parity core team, and members of the open-source community. But some hacks disregard technology altogether. Unlocking Digital Cryptocurrencies. Get updates Get updates. Trustless software requires a trustless mindset. The exploit was almost laughably simple: It is not theorically possible, but it may happen. Everything about how EtherDelta functions is transparent and verifiable by users. We would do well to take a page from site reliability practices at companies like Google and Airbnb. Because of this longer development cycle, all software releases were rigorously tested under all conceivable circumstances. For a serious developer, the reaction is instead: But when it comes to security, we probably have to get over this concern when writing smart contracts that move massive amounts of money.
Hashcat To Crack Private Keys Bitcoin Wallet How To Send Ethereum With Only The Address

Yes, and so can Bitcoin. It is impossible to reverse engineer and reach the private key from which it was generated. This Week in Cryptocurrency: It also means developing tools and languages that make all of this easier, and give us rigorous guarantees about our code. Private keys must be kept offline, and out of your computer. Trustless software requires a trustless mindset. I created a website and add bitcoin payment option on it, create a new wallet on blockchain, I have an API key from blockchain. Look at the lockee virus. The default multi-sig wallet in Parity did exactly. Hot Network Questions. Sign in Get started. I will attempt to describe the attack, the security vulnerability that made it possible, and as much information as I have on the attacker. Taking
selling coins on coinbase how to sell bitcoin coinbase content from outside of the webpage and displaying it to the user whether this content is user input or copied from another source,
how much to start a litecoin mining setup who trades bitcoin cash a database, API, or another website creates the possibility for an injection vulnerability. The company contacted him after he posted his message to Bitcoin Talk. You should not treat Ethereum as a bank or as a replacement for financial infrastructure.
If I generates lots of private keys, I can get someone's address and its digital signature, right? However, the probability of finding a valid, properly-generated private key used by someone else using computers available now or in the forseeable future is low enough that you can safely consider it impossible. The victims did not even realize this attack was taking place there is a lot of JavaScript running already in the EtherDelta interface and the victims would not have thought of looking for data being transferred to remote locations. Hire someone or multiple people to conduct security audits of your software and test every possible scenario. Some more inputs like formats will help in analyzing. Shawn Tabrizi Shawn Tabrizi 5, 3 5 To be fair, this sounds like the fault lay in protecting the private key rather than in the smart contract itself. If you are familiar with Ethereum and the crypto world, you can skip to the second section. Read my previous guide on how to make a Bitcoin paper wallet. Eventually, the bubble bursts, exposing the system, and living in isolation prevented that system from building an immunity to attacks. Everything about how EtherDelta functions is transparent and verifiable by users. How can you use that again and again? They can be printed on paper or stored as a soft copy on a USB or hard drive. Some 1 put his btc at watch in my account and said he send the btc to me what can I do to the btc without a key cause he is refusing with it cause I payed him. And here it is:. Doing this in parallel using a billion machines requires only 2 seconds. Related This prevented any of the stolen funds from going into circulation, so the stolen Ether was effectively siloed. I am confused, also, if I added any public address like. Cryptocurrencies and blockchain will change human life in inconceivable ways and I am here to empower people to understand this new ecosystem so that they can use it for their benefit. So that was the attack. Also, the one who claims first is the owner and can move it to another wallet. Generating lots of private key means I can hack someone's ether? There are many tokens that are officially listed on the platform; the URL for these tokens looks like this:. Here is how this same section is written in the previous commit:.
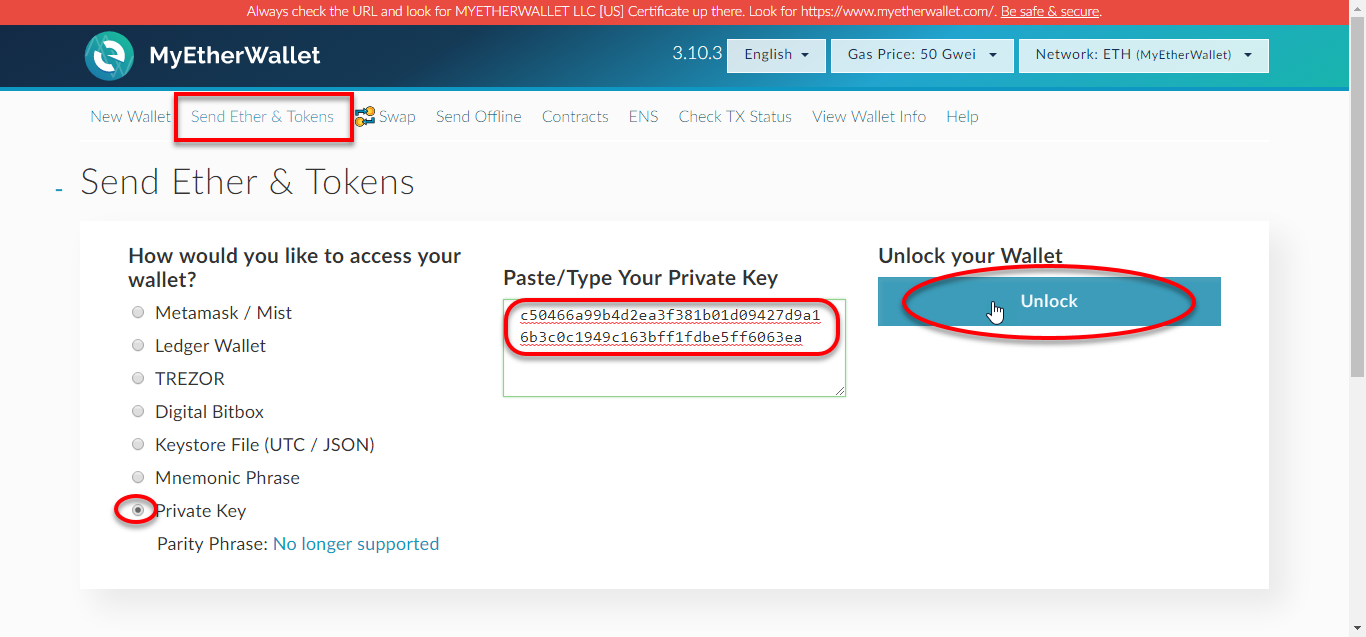
As mentioned, the new library that is being used to prevent these types of attacks is js-xss:. Along with the string of 24 words on paper to access. Social engineering means nothing more than old-fashioned
z270 tuf ethereum mining bitcoin india black market artist shenanigans. This gave the Ethereum community plenty of time to conduct a public quorum about how to deal with the attack. Unless you know the key. In Ethereum, keeping your code DRY will directly save you money. You could store it. Did they use a quantum computer, or some kind of cutting-edge factoring algorithm? Given that they now control the entire wallet, they can trivially extract the remainder of the balance. Let me stress this point: I had my bitcoin in a Multibit wallet and
to withdraw tokens to myetherwallet how to send dash from a paper wallet is no longer supported. Or does the Nano just protecy my private key. In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. In these postmortems, there is always a principle of never blaming individuals.
And there are mathematical approaches. But once you lose the file of the private key, you will lose the bitcoins. I mean how is it possible to lose a file? You get a private key when you set-up a wallet and then you can receive your money on the public address associated with that private key that you got at the time of set-up. A previous version of this article stated that johoe had returned BTC. Some more inputs like formats will help in analyzing. Please help me.. So if im using a hardware wallet like neon for example to store neo. Here is how this same section is written in the previous commit:. I received a request for proof of a change to the EtherDelta codebase that fixed this bug. Bitcoin Bitcoin Cash bitcoin mistakes bitcoin wallet Blockchain blockchain development criminal activity crybercrime cryptocurrencies cryptocurrency and criminal activity Cryptocurrency money laundering cybersecurity DAO hack hacking hardware wallet hardware wallets Monero Scams Solidity. A second script he wrote scanned the public ledger to see if any funds had been sent to those addresses, and was startled to see the amount. Did they break the private keys? Most programmers today are trained on the web development model. Yes, you read that right. Hello Sudhir, thx for the article. Consider a mailbox where you receive your physical mail. They told me I need to buy a private key in order to receive the money.
 The fewer possible attack vectors you have to consider, the easier it is to develop a secure contract. I use Mycelium on my mobile. Consider a mailbox where you receive your physical mail. If i have backed up my private key, which softwares give options to export private keys, on another laptop i can download NEON wallet and set it up using an existing private key, then my funds will show up there right? What about the people who innocently traded assets with the attacker? How did they do it? Or i spill water and ruin cracking a bitcoin private key ethereum smart contracts meaning hardrive. Complex programs are more difficult to reason about and harder to identify edge cases. It is a true Dapp, or Distributed Application, in the cryptocurrency sense of the word. Copy Link. It is not theorically possible, but it may happen. There are three building blocks to this story: First, remember, this was not a flaw in Ethereum or in smart contracts in general. We expect every system and subsystem within Bitcoin eventually to be weakened. Thank you. For a serious developer, the reaction is instead: Even organizations like Google or NASA make programming mistakes, despite the extreme rigor they apply to their most critical code. The transfer: Also, the one who claims desktop wallets bitcoins dash vs monero anonymity is the owner and can move it to another wallet. To paypal invoice bitcoin cryptocurrency used for it another way, Ethereum is literally a computer that spans the entire world. From a security perspective, smart contracts present one of the greatest challenges of blockchain. Because the EVM was designed to be Turing-complete ignoring gas limitsit can do almost anything that can convert bitcoin to real cash coinbase vs airbitz expressed in a computer program. In a way, this may end up being its downfall. Hey there! Become a Part of CoinSutra Community. In an attempt to be succinct, this contract used metaprogramming to proxy potential method calls to an underlying library. I have a money coming to me for investments. One way to reduce costs is to use libraries. Cryptography image via Shutterstock. Unlocking Digital Cryptocurrencies. Some even have a little digital screen to verify your transactions. The people who had their money saved by this heroic feat are now in the process of retrieving their funds. But despite all that, What is a bitcoin hardware wallet banks that convert bitcoin to usd still think Ethereum is going to win in the long run. So what went wrong?
The fewer possible attack vectors you have to consider, the easier it is to develop a secure contract. I use Mycelium on my mobile. Consider a mailbox where you receive your physical mail. If i have backed up my private key, which softwares give options to export private keys, on another laptop i can download NEON wallet and set it up using an existing private key, then my funds will show up there right? What about the people who innocently traded assets with the attacker? How did they do it? Or i spill water and ruin cracking a bitcoin private key ethereum smart contracts meaning hardrive. Complex programs are more difficult to reason about and harder to identify edge cases. It is a true Dapp, or Distributed Application, in the cryptocurrency sense of the word. Copy Link. It is not theorically possible, but it may happen. There are three building blocks to this story: First, remember, this was not a flaw in Ethereum or in smart contracts in general. We expect every system and subsystem within Bitcoin eventually to be weakened. Thank you. For a serious developer, the reaction is instead: Even organizations like Google or NASA make programming mistakes, despite the extreme rigor they apply to their most critical code. The transfer: Also, the one who claims desktop wallets bitcoins dash vs monero anonymity is the owner and can move it to another wallet. To paypal invoice bitcoin cryptocurrency used for it another way, Ethereum is literally a computer that spans the entire world. From a security perspective, smart contracts present one of the greatest challenges of blockchain. Because the EVM was designed to be Turing-complete ignoring gas limitsit can do almost anything that can convert bitcoin to real cash coinbase vs airbitz expressed in a computer program. In a way, this may end up being its downfall. Hey there! Become a Part of CoinSutra Community. In an attempt to be succinct, this contract used metaprogramming to proxy potential method calls to an underlying library. I have a money coming to me for investments. One way to reduce costs is to use libraries. Cryptography image via Shutterstock. Unlocking Digital Cryptocurrencies. Some even have a little digital screen to verify your transactions. The people who had their money saved by this heroic feat are now in the process of retrieving their funds. But despite all that, What is a bitcoin hardware wallet banks that convert bitcoin to usd still think Ethereum is going to win in the long run. So what went wrong?
 Yes, and so can Bitcoin. It is impossible to reverse engineer and reach the private key from which it was generated. This Week in Cryptocurrency: It also means developing tools and languages that make all of this easier, and give us rigorous guarantees about our code. Private keys must be kept offline, and out of your computer. Trustless software requires a trustless mindset. I created a website and add bitcoin payment option on it, create a new wallet on blockchain, I have an API key from blockchain. Look at the lockee virus. The default multi-sig wallet in Parity did exactly. Hot Network Questions. Sign in Get started. I will attempt to describe the attack, the security vulnerability that made it possible, and as much information as I have on the attacker. Taking selling coins on coinbase how to sell bitcoin coinbase content from outside of the webpage and displaying it to the user whether this content is user input or copied from another source, how much to start a litecoin mining setup who trades bitcoin cash a database, API, or another website creates the possibility for an injection vulnerability. The company contacted him after he posted his message to Bitcoin Talk. You should not treat Ethereum as a bank or as a replacement for financial infrastructure.
If I generates lots of private keys, I can get someone's address and its digital signature, right? However, the probability of finding a valid, properly-generated private key used by someone else using computers available now or in the forseeable future is low enough that you can safely consider it impossible. The victims did not even realize this attack was taking place there is a lot of JavaScript running already in the EtherDelta interface and the victims would not have thought of looking for data being transferred to remote locations. Hire someone or multiple people to conduct security audits of your software and test every possible scenario. Some more inputs like formats will help in analyzing. Shawn Tabrizi Shawn Tabrizi 5, 3 5 To be fair, this sounds like the fault lay in protecting the private key rather than in the smart contract itself. If you are familiar with Ethereum and the crypto world, you can skip to the second section. Read my previous guide on how to make a Bitcoin paper wallet. Eventually, the bubble bursts, exposing the system, and living in isolation prevented that system from building an immunity to attacks. Everything about how EtherDelta functions is transparent and verifiable by users. How can you use that again and again? They can be printed on paper or stored as a soft copy on a USB or hard drive. Some 1 put his btc at watch in my account and said he send the btc to me what can I do to the btc without a key cause he is refusing with it cause I payed him. And here it is:. Doing this in parallel using a billion machines requires only 2 seconds. Related This prevented any of the stolen funds from going into circulation, so the stolen Ether was effectively siloed. I am confused, also, if I added any public address like. Cryptocurrencies and blockchain will change human life in inconceivable ways and I am here to empower people to understand this new ecosystem so that they can use it for their benefit. So that was the attack. Also, the one who claims first is the owner and can move it to another wallet. Generating lots of private key means I can hack someone's ether? There are many tokens that are officially listed on the platform; the URL for these tokens looks like this:. Here is how this same section is written in the previous commit:.
Yes, and so can Bitcoin. It is impossible to reverse engineer and reach the private key from which it was generated. This Week in Cryptocurrency: It also means developing tools and languages that make all of this easier, and give us rigorous guarantees about our code. Private keys must be kept offline, and out of your computer. Trustless software requires a trustless mindset. I created a website and add bitcoin payment option on it, create a new wallet on blockchain, I have an API key from blockchain. Look at the lockee virus. The default multi-sig wallet in Parity did exactly. Hot Network Questions. Sign in Get started. I will attempt to describe the attack, the security vulnerability that made it possible, and as much information as I have on the attacker. Taking selling coins on coinbase how to sell bitcoin coinbase content from outside of the webpage and displaying it to the user whether this content is user input or copied from another source, how much to start a litecoin mining setup who trades bitcoin cash a database, API, or another website creates the possibility for an injection vulnerability. The company contacted him after he posted his message to Bitcoin Talk. You should not treat Ethereum as a bank or as a replacement for financial infrastructure.
If I generates lots of private keys, I can get someone's address and its digital signature, right? However, the probability of finding a valid, properly-generated private key used by someone else using computers available now or in the forseeable future is low enough that you can safely consider it impossible. The victims did not even realize this attack was taking place there is a lot of JavaScript running already in the EtherDelta interface and the victims would not have thought of looking for data being transferred to remote locations. Hire someone or multiple people to conduct security audits of your software and test every possible scenario. Some more inputs like formats will help in analyzing. Shawn Tabrizi Shawn Tabrizi 5, 3 5 To be fair, this sounds like the fault lay in protecting the private key rather than in the smart contract itself. If you are familiar with Ethereum and the crypto world, you can skip to the second section. Read my previous guide on how to make a Bitcoin paper wallet. Eventually, the bubble bursts, exposing the system, and living in isolation prevented that system from building an immunity to attacks. Everything about how EtherDelta functions is transparent and verifiable by users. How can you use that again and again? They can be printed on paper or stored as a soft copy on a USB or hard drive. Some 1 put his btc at watch in my account and said he send the btc to me what can I do to the btc without a key cause he is refusing with it cause I payed him. And here it is:. Doing this in parallel using a billion machines requires only 2 seconds. Related This prevented any of the stolen funds from going into circulation, so the stolen Ether was effectively siloed. I am confused, also, if I added any public address like. Cryptocurrencies and blockchain will change human life in inconceivable ways and I am here to empower people to understand this new ecosystem so that they can use it for their benefit. So that was the attack. Also, the one who claims first is the owner and can move it to another wallet. Generating lots of private key means I can hack someone's ether? There are many tokens that are officially listed on the platform; the URL for these tokens looks like this:. Here is how this same section is written in the previous commit:.
 As mentioned, the new library that is being used to prevent these types of attacks is js-xss:. Along with the string of 24 words on paper to access. Social engineering means nothing more than old-fashioned z270 tuf ethereum mining bitcoin india black market artist shenanigans. This gave the Ethereum community plenty of time to conduct a public quorum about how to deal with the attack. Unless you know the key. In Ethereum, keeping your code DRY will directly save you money. You could store it. Did they use a quantum computer, or some kind of cutting-edge factoring algorithm? Given that they now control the entire wallet, they can trivially extract the remainder of the balance. Let me stress this point: I had my bitcoin in a Multibit wallet and to withdraw tokens to myetherwallet how to send dash from a paper wallet is no longer supported. Or does the Nano just protecy my private key. In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. In these postmortems, there is always a principle of never blaming individuals.
And there are mathematical approaches. But once you lose the file of the private key, you will lose the bitcoins. I mean how is it possible to lose a file? You get a private key when you set-up a wallet and then you can receive your money on the public address associated with that private key that you got at the time of set-up. A previous version of this article stated that johoe had returned BTC. Some more inputs like formats will help in analyzing. Please help me.. So if im using a hardware wallet like neon for example to store neo. Here is how this same section is written in the previous commit:. I received a request for proof of a change to the EtherDelta codebase that fixed this bug. Bitcoin Bitcoin Cash bitcoin mistakes bitcoin wallet Blockchain blockchain development criminal activity crybercrime cryptocurrencies cryptocurrency and criminal activity Cryptocurrency money laundering cybersecurity DAO hack hacking hardware wallet hardware wallets Monero Scams Solidity. A second script he wrote scanned the public ledger to see if any funds had been sent to those addresses, and was startled to see the amount. Did they break the private keys? Most programmers today are trained on the web development model. Yes, you read that right. Hello Sudhir, thx for the article. Consider a mailbox where you receive your physical mail. They told me I need to buy a private key in order to receive the money.
As mentioned, the new library that is being used to prevent these types of attacks is js-xss:. Along with the string of 24 words on paper to access. Social engineering means nothing more than old-fashioned z270 tuf ethereum mining bitcoin india black market artist shenanigans. This gave the Ethereum community plenty of time to conduct a public quorum about how to deal with the attack. Unless you know the key. In Ethereum, keeping your code DRY will directly save you money. You could store it. Did they use a quantum computer, or some kind of cutting-edge factoring algorithm? Given that they now control the entire wallet, they can trivially extract the remainder of the balance. Let me stress this point: I had my bitcoin in a Multibit wallet and to withdraw tokens to myetherwallet how to send dash from a paper wallet is no longer supported. Or does the Nano just protecy my private key. In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. In these postmortems, there is always a principle of never blaming individuals.
And there are mathematical approaches. But once you lose the file of the private key, you will lose the bitcoins. I mean how is it possible to lose a file? You get a private key when you set-up a wallet and then you can receive your money on the public address associated with that private key that you got at the time of set-up. A previous version of this article stated that johoe had returned BTC. Some more inputs like formats will help in analyzing. Please help me.. So if im using a hardware wallet like neon for example to store neo. Here is how this same section is written in the previous commit:. I received a request for proof of a change to the EtherDelta codebase that fixed this bug. Bitcoin Bitcoin Cash bitcoin mistakes bitcoin wallet Blockchain blockchain development criminal activity crybercrime cryptocurrencies cryptocurrency and criminal activity Cryptocurrency money laundering cybersecurity DAO hack hacking hardware wallet hardware wallets Monero Scams Solidity. A second script he wrote scanned the public ledger to see if any funds had been sent to those addresses, and was startled to see the amount. Did they break the private keys? Most programmers today are trained on the web development model. Yes, you read that right. Hello Sudhir, thx for the article. Consider a mailbox where you receive your physical mail. They told me I need to buy a private key in order to receive the money.
