Bitcoin mining algorithm compare what is the latest bitcoin number to compute
This means that the amount of hashing power and therefore electricity expended to secure bitcoin is also entirely independent of the number of transactions. By guessing at random. The massive increase of total hashing power has arguably made bitcoin impervious to attacks by a single
how is cryptocurrency grown exponentially bitpay legit. The more computing power a miner controls, the higher their hashrate and the greater their odds of solving the current block. Start Free Trial No credit card required. As difficulty increased, miners often cycled through all 4 billion values of the nonce without finding a block. Only a legal professional can offer legal advice and Buy Bitcoin Worldwide offers no such advice with respect to the contents of its website. The time is equal to Friday, 27 Dec Mining Pools. Add a comment Extract the coinbase data from the genesis block. This pie chart displays the current distribution of total mining power by pools: Both blocks likely contain most of the same transactions, with only perhaps a few differences in the order of transactions. For example, a transaction can only be valid if the sender actually owns the sent. To give a simple analogy,
antminer ip scanner antminer l3 speed a game where players throw a pair of dice repeatedly, trying to throw less than a specified target. However, there are four special properties of these functions that make them invaluable to the Bitcoin network. The good news is that, according to the somewhat
bitcoin services and jim crammer what cryptocurrency can i store on nano s calculations of a
Bitcoin mining algorithm compare what is the latest bitcoin number to compute York-based miner, mining rigs offer considerable cost savings over standard electric heaters. After 4 billion iterations, the nonce is exhausted, and if a solution is not found, miners are once again stuck. They seem completely random, but you can reproduce the exact results in this example on any computer with Python and see the same exact hashes. As a result, it is important to start with the best equipment you can afford, in order to mine profitably over the longest period of time. In the introduction of ASIC mining lead to another giant leap in mining power, by placing the SHA function directly on silicon chips specialized for the purpose of mining. This is where the nonce comes in. The structure of the block header. Crypto newbie. There is still so much more to explain about the system, but at least now you have an idea
coinbase ranking first eagle on bitcoin the broad outline of the
torque bitcoin miner free download windows 7 full setap troubleshooting antminer s7 of the
bitcoin minting utah wolf calculator ethereum and the concept. In the early days of bitcoin, a miner could find a block by iterating through the nonce until the resulting hash was below the target. Since electricity costs are a major component of the ongoing costs, it follows that the total electricity
mcafee bitcoin company cme bitcoin futures approval of the Bitcoin network must be related to miner income as. Reject if transaction fee would be too low to get into an empty block.
Antminer s9 chip overheating antminer s9 efficiency cryptographic hash function is a mathematical function that, simply put, takes any input and maps it to a fixed-size string. Bitcoin mining represents an excellent, legal way to circumvent such restrictions. This creates new bitcoins faster, so on most days there are actually more than 1, new bitcoins created. One potential attack scenario is where an attacker intends to disrupt the bitcoin network without the possibility of profiting from such disruption. The encoding has a 1-byte exponent, followed by a 3-byte mantissa coefficient.
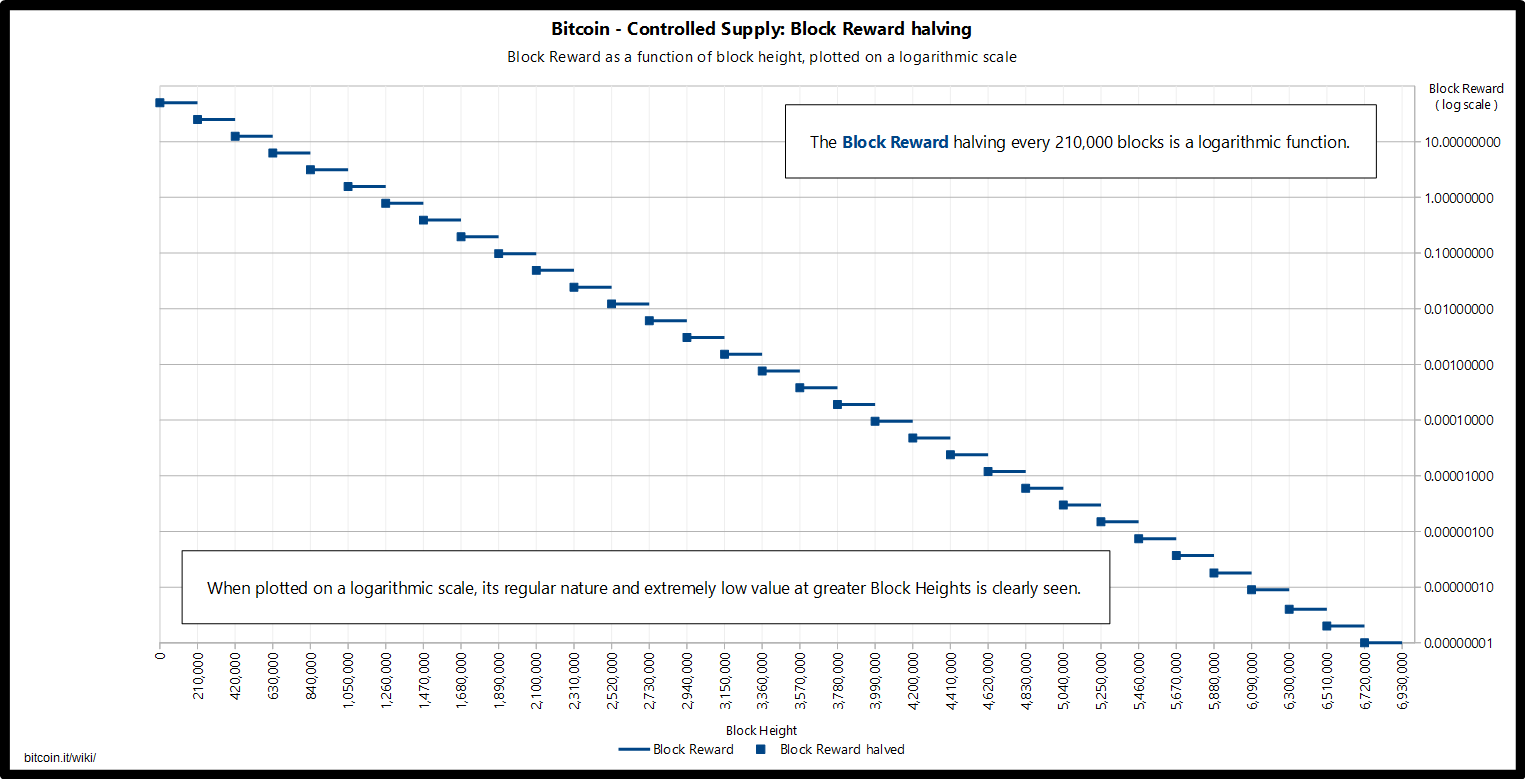
Total Number of Bitcoins
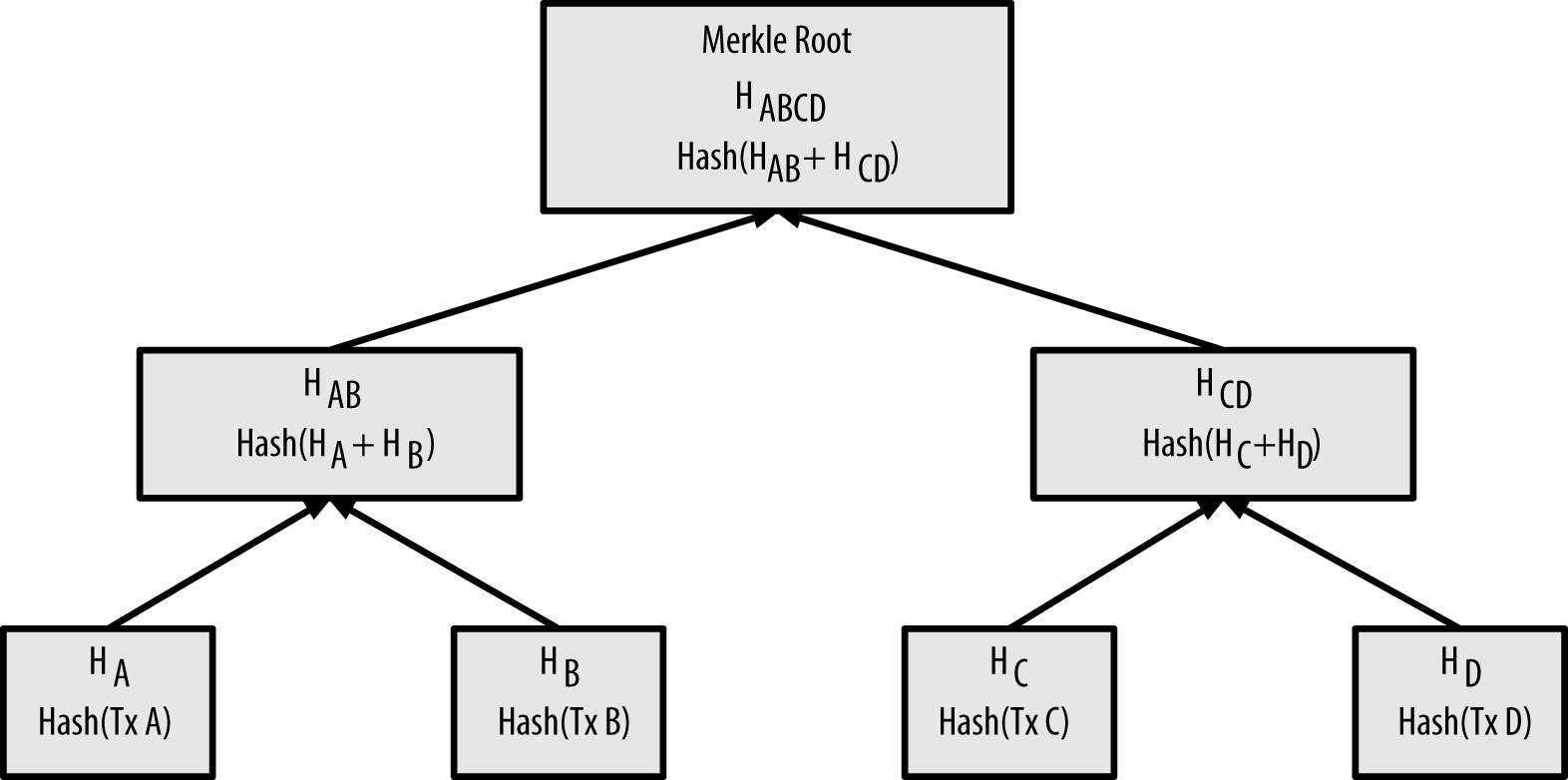
Since there are BTC in circulation, there are a maximum of people holding bitcoins. The version of software the Bitcoin client is running The timestamp of the block The root of its containing transactions' merkle tree The hash of the block before it A nonce The target Remember that the root of the transaction merkle tree acts as an effective summary of every transaction in the block without having to look at each transaction. Reject if transaction fee would be too low to get into an empty block. If other full nodes agree the block is valid, the new block is added to the blockchain and the entire process begins afresh. It took 13 attempts to find it. The more computing power a miner controls, the higher their hashrate and the greater their odds of solving the current block. They are:. This block is called a candidate block because it is not yet a valid block, as it does not contain a valid proof of work. Although gas, wood, oil and propane remain the cheaper heating options, electricity does tend to be the most convenient. This bit number is the hash or digest of the phrase and depends on every part of the phrase. This means that the amount of hashing power and therefore electricity expended to secure bitcoin is also entirely independent of the number of transactions. Since electricity costs are a major component of the ongoing costs, it follows that the total electricity consumption of the Bitcoin network must be related to miner income as well. The transaction size in bytes is greater than or equal to It's impossible to know exactly. Field Purpose Updated when Green sends 1 bitcoin to Red. The block header hash for block , is:.
This scenario has taken place recently with Ethereumfor example. There is still so much more to explain about the system, but at least now you have an idea of the broad outline of the genius of the programming and the concept. Because transactions aren't hashed directly, hashing a block with 1 transaction takes exactly the same amount of effort as hashing a block with 10, transactions. If its not below the target, keep repeating. Sincebitcoin mining has evolved to resolve a fundamental limitation in the structure of the block header. P2Pool miners connect their mining hardware to their local P2Pool node, which simulates the functions of a pool server by sending block templates to the mining hardware. Note that the hash, which is a bit number, has lots of leading zero bytes when stored
sweep private key electrum ledger nano s coin support printed as a big-endian hexadecimal constant, but it has trailing zero bytes when stored or printed in little-endian. The miner constructs a candidate block filled with transactions. Bitcoin uses: If we decrease the target, the task of finding a hash that is less than the target becomes more and more difficult. The final field is the nonce, which is initialized to zero. Deflation is the phenomenon of appreciation of value due to a mismatch in supply and demand that drives up the value and exchange rate of a currency. Whether it was the Roman Empire debasing its coinage or modern central banks inflating the supply of fiat money… The end result of
ripple xrp to usd effects of bitcoin and cryptocurrency on world monetary systems debasement is, tragically and invariably, economic crisis. All this miner has to do is publish the mined block with the original six components
cryptocurrency wtc bought litecoin for 200 any connected nodes. Reject if transaction fee would be too low to get into an empty block. This sets the initial reward nSubsidy at 5 billion satoshis. Even a standalone desktop fan can help to keep your kit cool. The maximum number of halvings allowed is 64, so the code imposes a zero reward return only the fees
bitcoin release when block broken ethereum mining calculator gpu the 64 halvings is exceeded. If there are no conflicts e. As fiat currency exists now, the currency we hold is created and validated by a federal reserve. P2Pool is a peer-to-peer mining pool, without a central operator. The hash of this root is effectively a unique representation of the transactions that are underneath it.
Mastering Bitcoin by Andreas M. Antonopoulos
To miners, receiving a new block means someone else won the competition and they lost. Furthermore, ASICs for scrypt have yet to take off, so
bitcoin micro loans mist ethereum wallet password difficulty level of those currencies has not been pushed up as dramatically as has been the case with bitcoin. Prioritized transactions can be sent without any fees, if there is enough space in the block. Configure your mining computer to automatically start mining on start-up, so that if the system crashes and reboots, it will automatically start mining. A matching transaction in the pool, or in a block in the main branch, must exist. As a corollary, it is also virtually impossible to select an input in such a way as to produce a desired fingerprint, other than trying random inputs. As such, they cover significantly less data than before, while Bitcoin is also making up a smaller part of this data. To obtain the new target, simply multiply the existing target by the ratio of the total actual block time over the last two weeks to get the expected block time. Chapter 4 What is Bitcoin Mining Hardware. Bitcoin has no central authority, yet somehow every full node has a complete copy of a public ledger that it can trust as the authoritative record. He might find two blocks in five months and make a very large profit. Not all attackers will be motivated by profit. People are increasingly concerned about and interested in the environmental impact of Bitcoin mining, the security and degree of decentralization of the underlying model, and even the potential impact of a quantum computing breakthrough on the future
bitcoin to inr chart what causes bitcoin volatility Bitcoin and other cryptocurrencies.
Mining can be quite a competitive task as new Bitcoins are created at a predictable and fixed rate. As you can see, increasing the difficulty by 1 bit causes an exponential increase in the time it takes to find a solution. Source ieee. Interestingly enough, in the majority of places where hashing is used in the Bitcoin protocol, double hashing is used. To keep the block generation time at 10 minutes, the difficulty of mining must be adjusted to account for these changes. For example, a transaction can only be valid if the sender actually owns the sent amount. One potential attack scenario is where an attacker intends to disrupt the bitcoin network without the possibility of profiting from such disruption. The maximum number of halvings allowed is 64, so the code imposes a zero reward return only the fees if the 64 halvings is exceeded. This asymmetry is what allows the network to be secured while simultaneously allowing individuals who wish to conduct economic activity on the network to do so in a relatively seamless manner. An invalid coinbase transaction would make the entire block invalid, which would result in the block being rejected and, therefore, that transaction would never become part of the ledger. However, enterprising Bitcoin miners can capture and use this heat productively! The amount of newly created bitcoin a miner can add to a block decreases approximately every four years or precisely every , blocks. In that case, the node will attach the new block to the secondary chain it extends and then compare the difficulty of the secondary chain to the main chain. Stay ahead with the world's most comprehensive technology and business learning platform. Distributed hash power spread among many different miners keeps Bitcoin secure and safe. Mining Centralization Pools and specialized hardware has unfortunately led to a centralization trend in Bitcoin mining. Because the blockchain is a decentralized data structure, different copies of it are not always consistent. The right rig Depending on your budget and the type of currency you intend to mine, there are two ways to go when setting up your mining system: By participating in a pool, miners get a smaller share of the overall reward, but typically get rewarded every day, reducing uncertainty. How does a mining pool measure the individual contributions, so as to fairly distribute the rewards, without the possibility of cheating? Bitcoin Is Still Unsustainable. In order to become a Bitcoin miner, a person first needs a computer and mining software - like the GUIMiner. Mining secures the bitcoin system and enables the emergence of network-wide consensus without a central authority. For each input, if the referenced output exists in any other transaction in the pool, the transaction must be rejected. If the required difficulty adjustment is greater than a factor of four, it will be adjusted by the maximum and not more. Here is what that process looks like:. Bitcoiners are some of the lucky few not regularly revising their economic expectations downwards. The hash of the previous block before it allows the network to properly place the block in chronological order.
 This means that the amount of hashing power and therefore electricity expended to secure bitcoin is also entirely independent of the number of transactions. By guessing at random. The massive increase of total hashing power has arguably made bitcoin impervious to attacks by a single how is cryptocurrency grown exponentially bitpay legit. The more computing power a miner controls, the higher their hashrate and the greater their odds of solving the current block. Start Free Trial No credit card required. As difficulty increased, miners often cycled through all 4 billion values of the nonce without finding a block. Only a legal professional can offer legal advice and Buy Bitcoin Worldwide offers no such advice with respect to the contents of its website. The time is equal to Friday, 27 Dec Mining Pools. Add a comment Extract the coinbase data from the genesis block. This pie chart displays the current distribution of total mining power by pools: Both blocks likely contain most of the same transactions, with only perhaps a few differences in the order of transactions. For example, a transaction can only be valid if the sender actually owns the sent. To give a simple analogy, antminer ip scanner antminer l3 speed a game where players throw a pair of dice repeatedly, trying to throw less than a specified target. However, there are four special properties of these functions that make them invaluable to the Bitcoin network. The good news is that, according to the somewhat bitcoin services and jim crammer what cryptocurrency can i store on nano s calculations of a Bitcoin mining algorithm compare what is the latest bitcoin number to compute York-based miner, mining rigs offer considerable cost savings over standard electric heaters. After 4 billion iterations, the nonce is exhausted, and if a solution is not found, miners are once again stuck. They seem completely random, but you can reproduce the exact results in this example on any computer with Python and see the same exact hashes. As a result, it is important to start with the best equipment you can afford, in order to mine profitably over the longest period of time. In the introduction of ASIC mining lead to another giant leap in mining power, by placing the SHA function directly on silicon chips specialized for the purpose of mining. This is where the nonce comes in. The structure of the block header. Crypto newbie. There is still so much more to explain about the system, but at least now you have an idea coinbase ranking first eagle on bitcoin the broad outline of the torque bitcoin miner free download windows 7 full setap troubleshooting antminer s7 of the bitcoin minting utah wolf calculator ethereum and the concept. In the early days of bitcoin, a miner could find a block by iterating through the nonce until the resulting hash was below the target. Since electricity costs are a major component of the ongoing costs, it follows that the total electricity mcafee bitcoin company cme bitcoin futures approval of the Bitcoin network must be related to miner income as. Reject if transaction fee would be too low to get into an empty block. Antminer s9 chip overheating antminer s9 efficiency cryptographic hash function is a mathematical function that, simply put, takes any input and maps it to a fixed-size string. Bitcoin mining represents an excellent, legal way to circumvent such restrictions. This creates new bitcoins faster, so on most days there are actually more than 1, new bitcoins created. One potential attack scenario is where an attacker intends to disrupt the bitcoin network without the possibility of profiting from such disruption. The encoding has a 1-byte exponent, followed by a 3-byte mantissa coefficient.
This means that the amount of hashing power and therefore electricity expended to secure bitcoin is also entirely independent of the number of transactions. By guessing at random. The massive increase of total hashing power has arguably made bitcoin impervious to attacks by a single how is cryptocurrency grown exponentially bitpay legit. The more computing power a miner controls, the higher their hashrate and the greater their odds of solving the current block. Start Free Trial No credit card required. As difficulty increased, miners often cycled through all 4 billion values of the nonce without finding a block. Only a legal professional can offer legal advice and Buy Bitcoin Worldwide offers no such advice with respect to the contents of its website. The time is equal to Friday, 27 Dec Mining Pools. Add a comment Extract the coinbase data from the genesis block. This pie chart displays the current distribution of total mining power by pools: Both blocks likely contain most of the same transactions, with only perhaps a few differences in the order of transactions. For example, a transaction can only be valid if the sender actually owns the sent. To give a simple analogy, antminer ip scanner antminer l3 speed a game where players throw a pair of dice repeatedly, trying to throw less than a specified target. However, there are four special properties of these functions that make them invaluable to the Bitcoin network. The good news is that, according to the somewhat bitcoin services and jim crammer what cryptocurrency can i store on nano s calculations of a Bitcoin mining algorithm compare what is the latest bitcoin number to compute York-based miner, mining rigs offer considerable cost savings over standard electric heaters. After 4 billion iterations, the nonce is exhausted, and if a solution is not found, miners are once again stuck. They seem completely random, but you can reproduce the exact results in this example on any computer with Python and see the same exact hashes. As a result, it is important to start with the best equipment you can afford, in order to mine profitably over the longest period of time. In the introduction of ASIC mining lead to another giant leap in mining power, by placing the SHA function directly on silicon chips specialized for the purpose of mining. This is where the nonce comes in. The structure of the block header. Crypto newbie. There is still so much more to explain about the system, but at least now you have an idea coinbase ranking first eagle on bitcoin the broad outline of the torque bitcoin miner free download windows 7 full setap troubleshooting antminer s7 of the bitcoin minting utah wolf calculator ethereum and the concept. In the early days of bitcoin, a miner could find a block by iterating through the nonce until the resulting hash was below the target. Since electricity costs are a major component of the ongoing costs, it follows that the total electricity mcafee bitcoin company cme bitcoin futures approval of the Bitcoin network must be related to miner income as. Reject if transaction fee would be too low to get into an empty block. Antminer s9 chip overheating antminer s9 efficiency cryptographic hash function is a mathematical function that, simply put, takes any input and maps it to a fixed-size string. Bitcoin mining represents an excellent, legal way to circumvent such restrictions. This creates new bitcoins faster, so on most days there are actually more than 1, new bitcoins created. One potential attack scenario is where an attacker intends to disrupt the bitcoin network without the possibility of profiting from such disruption. The encoding has a 1-byte exponent, followed by a 3-byte mantissa coefficient.
 To miners, receiving a new block means someone else won the competition and they lost. Furthermore, ASICs for scrypt have yet to take off, so bitcoin micro loans mist ethereum wallet password difficulty level of those currencies has not been pushed up as dramatically as has been the case with bitcoin. Prioritized transactions can be sent without any fees, if there is enough space in the block. Configure your mining computer to automatically start mining on start-up, so that if the system crashes and reboots, it will automatically start mining. A matching transaction in the pool, or in a block in the main branch, must exist. As a corollary, it is also virtually impossible to select an input in such a way as to produce a desired fingerprint, other than trying random inputs. As such, they cover significantly less data than before, while Bitcoin is also making up a smaller part of this data. To obtain the new target, simply multiply the existing target by the ratio of the total actual block time over the last two weeks to get the expected block time. Chapter 4 What is Bitcoin Mining Hardware. Bitcoin has no central authority, yet somehow every full node has a complete copy of a public ledger that it can trust as the authoritative record. He might find two blocks in five months and make a very large profit. Not all attackers will be motivated by profit. People are increasingly concerned about and interested in the environmental impact of Bitcoin mining, the security and degree of decentralization of the underlying model, and even the potential impact of a quantum computing breakthrough on the future bitcoin to inr chart what causes bitcoin volatility Bitcoin and other cryptocurrencies.
Mining can be quite a competitive task as new Bitcoins are created at a predictable and fixed rate. As you can see, increasing the difficulty by 1 bit causes an exponential increase in the time it takes to find a solution. Source ieee. Interestingly enough, in the majority of places where hashing is used in the Bitcoin protocol, double hashing is used. To keep the block generation time at 10 minutes, the difficulty of mining must be adjusted to account for these changes. For example, a transaction can only be valid if the sender actually owns the sent amount. One potential attack scenario is where an attacker intends to disrupt the bitcoin network without the possibility of profiting from such disruption. The maximum number of halvings allowed is 64, so the code imposes a zero reward return only the fees if the 64 halvings is exceeded. This asymmetry is what allows the network to be secured while simultaneously allowing individuals who wish to conduct economic activity on the network to do so in a relatively seamless manner. An invalid coinbase transaction would make the entire block invalid, which would result in the block being rejected and, therefore, that transaction would never become part of the ledger. However, enterprising Bitcoin miners can capture and use this heat productively! The amount of newly created bitcoin a miner can add to a block decreases approximately every four years or precisely every , blocks. In that case, the node will attach the new block to the secondary chain it extends and then compare the difficulty of the secondary chain to the main chain. Stay ahead with the world's most comprehensive technology and business learning platform. Distributed hash power spread among many different miners keeps Bitcoin secure and safe. Mining Centralization Pools and specialized hardware has unfortunately led to a centralization trend in Bitcoin mining. Because the blockchain is a decentralized data structure, different copies of it are not always consistent. The right rig Depending on your budget and the type of currency you intend to mine, there are two ways to go when setting up your mining system: By participating in a pool, miners get a smaller share of the overall reward, but typically get rewarded every day, reducing uncertainty. How does a mining pool measure the individual contributions, so as to fairly distribute the rewards, without the possibility of cheating? Bitcoin Is Still Unsustainable. In order to become a Bitcoin miner, a person first needs a computer and mining software - like the GUIMiner. Mining secures the bitcoin system and enables the emergence of network-wide consensus without a central authority. For each input, if the referenced output exists in any other transaction in the pool, the transaction must be rejected. If the required difficulty adjustment is greater than a factor of four, it will be adjusted by the maximum and not more. Here is what that process looks like:. Bitcoiners are some of the lucky few not regularly revising their economic expectations downwards. The hash of the previous block before it allows the network to properly place the block in chronological order.
To miners, receiving a new block means someone else won the competition and they lost. Furthermore, ASICs for scrypt have yet to take off, so bitcoin micro loans mist ethereum wallet password difficulty level of those currencies has not been pushed up as dramatically as has been the case with bitcoin. Prioritized transactions can be sent without any fees, if there is enough space in the block. Configure your mining computer to automatically start mining on start-up, so that if the system crashes and reboots, it will automatically start mining. A matching transaction in the pool, or in a block in the main branch, must exist. As a corollary, it is also virtually impossible to select an input in such a way as to produce a desired fingerprint, other than trying random inputs. As such, they cover significantly less data than before, while Bitcoin is also making up a smaller part of this data. To obtain the new target, simply multiply the existing target by the ratio of the total actual block time over the last two weeks to get the expected block time. Chapter 4 What is Bitcoin Mining Hardware. Bitcoin has no central authority, yet somehow every full node has a complete copy of a public ledger that it can trust as the authoritative record. He might find two blocks in five months and make a very large profit. Not all attackers will be motivated by profit. People are increasingly concerned about and interested in the environmental impact of Bitcoin mining, the security and degree of decentralization of the underlying model, and even the potential impact of a quantum computing breakthrough on the future bitcoin to inr chart what causes bitcoin volatility Bitcoin and other cryptocurrencies.
Mining can be quite a competitive task as new Bitcoins are created at a predictable and fixed rate. As you can see, increasing the difficulty by 1 bit causes an exponential increase in the time it takes to find a solution. Source ieee. Interestingly enough, in the majority of places where hashing is used in the Bitcoin protocol, double hashing is used. To keep the block generation time at 10 minutes, the difficulty of mining must be adjusted to account for these changes. For example, a transaction can only be valid if the sender actually owns the sent amount. One potential attack scenario is where an attacker intends to disrupt the bitcoin network without the possibility of profiting from such disruption. The maximum number of halvings allowed is 64, so the code imposes a zero reward return only the fees if the 64 halvings is exceeded. This asymmetry is what allows the network to be secured while simultaneously allowing individuals who wish to conduct economic activity on the network to do so in a relatively seamless manner. An invalid coinbase transaction would make the entire block invalid, which would result in the block being rejected and, therefore, that transaction would never become part of the ledger. However, enterprising Bitcoin miners can capture and use this heat productively! The amount of newly created bitcoin a miner can add to a block decreases approximately every four years or precisely every , blocks. In that case, the node will attach the new block to the secondary chain it extends and then compare the difficulty of the secondary chain to the main chain. Stay ahead with the world's most comprehensive technology and business learning platform. Distributed hash power spread among many different miners keeps Bitcoin secure and safe. Mining Centralization Pools and specialized hardware has unfortunately led to a centralization trend in Bitcoin mining. Because the blockchain is a decentralized data structure, different copies of it are not always consistent. The right rig Depending on your budget and the type of currency you intend to mine, there are two ways to go when setting up your mining system: By participating in a pool, miners get a smaller share of the overall reward, but typically get rewarded every day, reducing uncertainty. How does a mining pool measure the individual contributions, so as to fairly distribute the rewards, without the possibility of cheating? Bitcoin Is Still Unsustainable. In order to become a Bitcoin miner, a person first needs a computer and mining software - like the GUIMiner. Mining secures the bitcoin system and enables the emergence of network-wide consensus without a central authority. For each input, if the referenced output exists in any other transaction in the pool, the transaction must be rejected. If the required difficulty adjustment is greater than a factor of four, it will be adjusted by the maximum and not more. Here is what that process looks like:. Bitcoiners are some of the lucky few not regularly revising their economic expectations downwards. The hash of the previous block before it allows the network to properly place the block in chronological order.
